― John Green
“Oh, Wikipedia, with your tension between those who would share knowledge and those who would destroy it.”

― John Green
“Oh, Wikipedia, with your tension between those who would share knowledge and those who would destroy it.”
The computer as we know it today had its beginning with a 19th century English mathematics professor name Charles Babbage. He designed the Analytical Engine and it was this design that the basic framework of the computers of today are based on. In its most basic form a computer is any device which aids humans in performing various kinds of computations or calculations. Every computer supports some form of input, processing, and output. Regardless, this is what computing is all about, in a nutshell. We input information; the computer processes it according to its basic logic or the program currently running, and outputs the results.

Source: http://www.google.com/image
First Generation Computers (1940 – 1950) – Vacuum Tubes
The first computers used vacuum tubes for circuitry and magnetic drums for memory, and were often enormous, taking up entire rooms. They were very expensive to operate and in addition to using a great deal of electricity, generated a lot of heat, which was often the cause of malfunctions. The ENIAC (Electronic Numerical Integrator and Computer) computers are examples of first-generation computing devices. It was digital, although it didn’t operate with binary code, and was re-programmable to solve a complete range of computing problems.
In 1937 the first electronic digital computer was built by Dr. John V. Atanasoff and Clifford Berry. It was called the Atanasoff-Berry Computer (ABC). In 1943 an electronic computer name the Colossus was built for the military. Other similar computers developments of this era included German Z3, LEO, Harvard Mark I, and UNIVAC.

Source: http://www.google.com/image
Second Generation Computers (1955 – 1960) – Transistors
The second generation of computers came about thanks to the invention of the transistor, which was more reliable than vacuum tubes. Transistor computers consumed far less power, produced far less heat, and were much smaller compared to the first generation, albeit still big by today’s standards. The transistor allows computers to become smaller, faster, cheaper, energy-efficient and reliable than their first-generation predecessors. Though the transistor still generated a great deal of heat that subjected the computer to damage, it was a vast improvement over the vacuum tube.
The first transistor computer was created at the University of Manchester in 1953. In this generation, magnetic cores were used as primary memory and magnetic tape and magnetic disks as secondary storage devices.The most popular of transistor computers was IBM 1401. IBM also created the first disk drive in 1956, the IBM 350 RAMAC.

Source: http://www.google.com/image
Third Generation (1964-1971) Integrated Circuits
The invention of integrated circuit brought us the third generation of computers. Transistors were miniaturized and placed on silicon chips, called semiconductors, which drastically increased the speed and efficiency of computers.With this invention, computers became smaller and they are able to run many different programs at the same time. This also started the ongoing process of integrating an ever larger number of transistors onto a single microchip.
As a result of the various improvements to the development of the computer we have seen the computer being used in all areas of life. In 1980, Microsoft Disk Operating System (MS-Dos) was born and in 1981 IBM introduced the personal computer (PC) for home and office use. Three years later Apple gave us the Macintosh computer with its icon driven interface and the 90s gave us Windows operating system. It is a very useful tool that will continue to experience new development as time passes.

Source: http://www.google.com/image
Fourth Generation (1971-Present) – Microprocessors
The microprocessor brought the fourth generation of computers, as thousands of integrated circuits were built onto a single silicon chip. What in the first generation filled an entire room could now fit in the palm of the hand. The Intel 4004 chip, developed in 1971, located all the components of the computer from the central processing unit and memory to input/output controls on a single chip. The advent of the microprocessor spawned the evolution of the microcomputers, the kind that would eventually become personal computers that we are familiar with today.
In this generation time sharing, real time, networks, Distributed Operating System (DOS) were used. All the Higher level languages like C and C++, DBASE etc. also been used in this generation. In 1981, IBM introduced its first computer for the home user, and in 1984 Apple introduced the Macintosh. Microprocessors also moved out of the realm of desktop computers and into many areas of life as more and more everyday products began to use microprocessors.
As these small computers became more powerful, they could be linked together to form networks, which eventually led to the development of the Internet. Fourth generation computers also saw the development of GUIs, the mouse and handheld devices.

Source: http://www.google.com/image
Fifth Generation (Present and Beyond) – Artificial Intelligence
Fifth generation computing devices, based on AI (Artificial Intelligence), are still in development, though there are some applications, such as voice recognition, that are being used today. AI is an emerging branch in computer science, which interprets means and method of making computers think like human beings. The use of parallel processing and superconductors is helping to make artificial intelligence a reality. AI includes robotics, neural networks, game playing, development of expert systems to make decisions in real life situations and natural language understanding and generation.
Quantum computation and molecular and nanotechnology will radically change the face of computers in years to come. The goal of fifth generation computing is to develop devices that respond to natural language input and are capable of learning and self-organization.
Read more:
http://www.historyofcomputer.org/
http://people.bu.edu/baws/brief%20computer%20history.html
http://www.webopedia.com/DidYouKnow/Hardware_Software/2002/FiveGenerations.asp
http://www.tutorialspoint.com/computer_fundamentals/computer_generations.htm
Computer virus is a harmful software program written intentionally to enter a computer without the user’s permission or knowledge. It has the ability to replicate itself, thus continuing to spread. Some viruses do little but replicate, while others can cause severe harm or adversely affect the program and performance of the system. A virus should never be assumed harmless and left on a system.
There are different types of viruses which can be classified according to their origin, techniques, types of files they infect, where they hide, the kind of damage they cause, the type of operating system, or platform they attack. Let us have a look at few of them.
1. Boot Sector Virus

Source: http://www.makeuseof.com/
Boot sector viruses became popular because of the use of floppy disks to boot a computer which the virus attaches itself to the first part of the hard disk that is read by the computer upon boot up. The widespread usage of the Internet and the death of the floppy have made other means of virus transmission more effective.
This type of virus affects the boot sector of a hard disk. This is a crucial part of the disk, in which information of the disk itself is stored along with a program that makes it possible to boot (start) the computer from the disk. Examples of the boot sector viruses are Polyboot.B and AntiEXE. To protect, the best way of avoiding boot sector viruses is to ensure that floppy disks are write-protected. Also, never start your computer with an unknown floppy disk in the disk drive.
2. Browser Hijacker
Source: http://www.makeuseof.com/
This type of virus, which can spread itself in numerous ways including voluntary download, effectively hijacks certain browser functions, usually in the form of re-directing the user automatically to particular sites. It’s usually assumed that this tactic is designed to increase revenue from web advertisements. There are a lot of such viruses, and they usually have “search” included somewhere in their description. CoolWebSearch may be the most well known example, but others are nearly as common.
3. Direct Action Virus
This type of virus, unlike most, only comes into action when the file containing the virus is executed. The payload is delivered and then the virus essentially becomes dormant; it takes no other action unless an infected file is executed again.
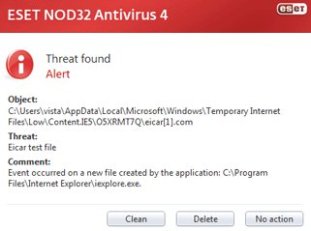
Most viruses do not use the direct action method of reproduction simply because it is not prolific, but viruses of this type have done damage in the past. The Vienna virus, which briefly threatened computers in 1988, is one such example of a direct action virus. By install an antivirus scanner, it will help to protect your computer. However, this type of virus has minimal effect on the computer’s performance.
4. File Infector Virus
Source: http://www.makeuseof.com/
Perhaps the most common type of virus, the file infector takes root in a host file and then begins its operation when the file is executed. The virus may completely overwrite the file that it infects, or may only replace parts of the file, or may not replace anything but instead re-write the file so that the virus is executed rather than the program the user intended.
Although called a “file virus” the definition doesn’t apply to all viruses in all files generally for example, the macro virus below is not referred to by the file virus. Instead, the definition is usually meant to refer only to viruses which use an executable file format, such as .exe, as their host.
5. Macro Virus
Macro viruses are viruses that use another application’s macro programming language to distribute themselves. Macro viruses infect files that are created using certain applications or programs that contain macros, like .doc, .xls, .pps, .mdb, etc. These viruses automatically infect the file that contains macros, and also infects the templates and documents that the file contains. It is referred to as a type of e-mail virus.
The most well known macro virus is probably Melissa, a Word document supposedly containing the passwords to pornographic websites. The virus also exploited Word’s link to Microsoft Outlook in order to automatically email copies of it. The best protection technique is to avoid opening e-mails from unknown senders. Also, disabling macros can help to protect your useful data.
6. Multipartite Virus
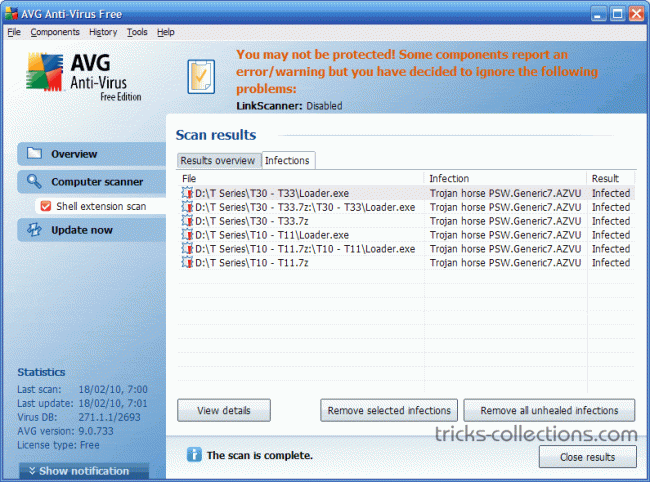
While some viruses are happy to spread via one method or deliver a single payload, multipartite viruses want it all. These viruses spread in multiple ways possible. A virus of this type may spread in multiple ways, and it may take different actions on an infected computer depending on variables, such as the operating system installed or the existence of certain files. Examples of this virus are Invader, Flip and Tequila. In the event to protect computer from this virus, you need to clean the boot sector and also the disk to get rid of the virus and then reload all the data in it. However, ensure that the data is clean.
7. Polymorphic Virus

Source: http://www.makeuseof.com/
A polymorphic virus not only replicates itself by creating multiple files of it, but it also changes its digital signature every time it replicates. Polymorphic viruses encrypt or encode themselves in a different way (using different algorithms and encryption keys) every time they infect a system. This makes it impossible for antivirus software to find them using string or signature searches (because they are different in each encryption). The virus then goes on to create a large number of copies.
The goal of this trickery is evasion. Antivirus programs often find viruses by the specific code used. Obscuring or changing the code of a virus can help it avoid detection. Polymorphic Viruses examples are Elkern, Marburg, Satan Bug and Tuareg. And for protection, to install a high-end antivirus as the normal ones are incapable of detecting this type of virus.
8. Memory Resident Viruses
Memory Resident Viruses reside in a computers volatile memory (RAM). They are initiated from a virus which runs on the computer and they stay in memory after its initiating program closes. A resident virus can be compared to a direct payload virus, which does not insert itself into the system’s memory and therefore only takes action when an infected file is executed. These viruses fix themselves in the computer memory and get activated whenever the OS runs and infects all the files that are then opened. Examples of Memory Resident Viruses are Randex, CMJ, Meve, and MrKlunky and protection against this virus a computer should be install with an antivirus program.
9. Web Scripting Virus
Many web pages include complex codes in order to create an interesting and interactive content. Displaying online video in your browser, for example, requires the execution of a specific code language that provides both the video itself and the player interface. Of course, this code can sometimes be exploited, making it possible for a virus to infect a computer or take actions on a computer through a website. Although malicious sites are sometimes created with purposely infected code, many such cases of virus exist because of code inserted into a site without the webmaster’s knowledge. For example, JS Fortnight is a virus that spreads through malicious e-mails. To protect, install the Microsoft tool application that is a default feature in Windows 2000, Windows 7 and Vista. Scan the computer with this application.
10. Trojan Horse
Source: http://www.google.com/image
Trojan Horse, which unlike viruses, do not reproduce by infecting other files, nor do they self-replicate like worms. In fact, it is a program which disguises itself as a useful program or application. A Trojan horse program has the appearance of having a useful and desired function. While it may advertise its activity after launching, this information is not apparent to the user beforehand. Secretly the program performs other, undesired functions. A Trojan Horse must be sent by someone or carried by another program and may arrive in the form of a joke program or software of some sort. The malicious functionality of a Trojan Horse may be anything undesirable for a computer user, including data destruction or compromising a system by providing a means for another computer to gain access, thus bypassing normal access controls.
11. Worms
A worm is a program that makes and facilitates the distribution of copies of itself; for example, from one disk drive to another, or by copying itself using email or another transport mechanism. The worm may do damage and compromise the security of the computer. It may arrive via exploitation of system vulnerability or by clicking on an infected e-mail. Examples of worms are PSWBugbear.B, Lovgate.F, Trile.C, Sobig.D, Mapson and to protect, installing an updated version of antivirus will be able to prevent your computer from damage.
12. Logic Bombs/Time Bombs
These are viruses which are programmed to initiate at a specific date or when a specific event occurs. Some examples are a virus which deletes your photos on any events such dinner etc., or a virus which deletes a database table if a certain employee gets fired.
They are not considered viruses because they do not replicate. They are not even programs in their own right, but rather camouflaged segments of other programs. They are only executed when a certain predefined condition is met. Their objective is to destroy data on the computer once certain conditions have been met. Logic bombs go undetected until launched, the results can be destructive, and your entire data can be deleted.
Read More…
http://www.makeuseof.com/tag/types-computer-viruses-watch/
http://antivirus-software.topchoicereviews.com/types-of-viruses.html
http://www.buzzle.com/articles/different-types-of-computer-viruses.html

Source: http://www.airasia.com
Internet is a global system network that uses the standard Internet Protocol (IP) to serve billions of users worldwide. It is a network that consists of millions of private, public, academic, business, and government networks, of local to global scope, that are linked by a broad array of electronic, wireless and optical networking technologies. The Internet carries an extensive range of information resources and services, such as the inter-linked hypertext documents of the World Wide Web (WWW) and the infrastructure to support email.
Air Asia is one of the award winning and largest low fare airlines in Asia expanding rapidly since 2001. With a fleet of 72 air crafts, Air Asia flies to over 61 domestic and international destinations with 108 routes, and operates over 400 flights daily from hubs located in Malaysia, Thailand, and Indonesia. Today, Air Asia has flown over 55 million guests across the region and continues to create more extensive route network through its associate companies. Air Asia believes in the no-frills, hassle-free, low fare business concept and feels that keeping costs low requires high efficiency in every part of the business. Through the corporate philosophy of “Now Everyone Can Fly”, Air Asia has sparked a revolution in air travel with more people around the region choosing Air Asia as their preferred choice of transport. Air Asia has fostered a dependency on Internet technology for its operational and strategic management, and provides an online ticket booking services to traveler online.

Source: http://www.airasia.com
In today globalize economy; information technology has driven fundamental changes in the nature and application of technology in business. The implementation of information technology in its value chain provides powerful strategic and tactical tools for Air Asia, which if properly applied and used, could bring great advantages in promoting and strengthening the competitive advantages.
Air Asia has currently adopted information technologies strategically to integrate the operations and coordinate all the business and management functions. The followings are few system implementations that Air Asia has done in its marketing and sales activities as well as operation activity in the value chain.
Yield Management System (YMS). The system anticipates and reacts to the behavior of customers to maximize the revenue. Taking into account the operating cost and aids Air Asia to optimize prices and allocate capacity to maximize the expected revenues by 2 levels; seats are available at various prices in different points of time and adjusting prices for routes that have a higher demand compared to others. Results increased revenue (3-4%) by taking advantage of the forecast of the high-low demand patterns, lower prices as YMS has aided Air Asia to increase the revenue by offering higher discounts, more frequently during off-peak times while raising prices only marginally for peak times.
Computer Reservation System (CRS). It is an integrated web enabled reservation and inventory system suite powered by Navitaire Open Skies technology that includes Internet, call center, and airport departure control functionality. CRS fulfilled the unique needs of Air Asia implementing a low-cost business model to transform the business process to efficiently streamline operations.
Enterprise Resource Planning System (ERP). ERP solution is powered by Microsoft Business Solutions (MBS) on Microsoft technology platform which is implemented by Avanade consultants in 2005. With the robust ERP technology platform, Air Asia is able to successfully maintain process integrity, reduce financial month-end closing processing time, speeds up reporting and data retrieval process.
With the information technology system is fully utilized to embark the Asia market, Air Asia has proven the technology increase its sales. In 2012, Air Asia reported profit up to RM1.88 billions with an increasing of 168% profit margin from 2011.
Learn More…
eAirlines: Strategic and Tactial Use of ICTs in the Airline Industry. Dimitrious Buhalis. University of Surrey. 2004.
The future of CRM in the airline industry: A new paradigm for customer management. IBM Institute for Business Value. 2002.
AirAsia Corporate Website. http://www.airasia.com.
shinebrightlikeadiamonds
Celebrating Life, Spirituality, Creativity and Kindness!
programmer, photo junkie, quirky
sarang-do-yeong-won-hal-soo-itt-neun-de (Love Can Last Forever)